EDIT: As of 11/18/2024 - This post has been restored pretty much "as is" for now.
I'll be back with more updates soon.

Disclaimer: This post is for beginner to intermediate engineers and developers, maybe even for some seniors & experts. You guys might actually learn a thing or two if you don’t already ‘know everything’. LOL I’ve decided to break this blog post into several parts because there are A LOT of technologies involved and I want to cover them all fairly. Finally, the resources I share here are not paid promotions and so I just hope this helps you like it helped me.
What is Wazuh?
Prepare to be amazed as we delve into the extraordinary world of Wazuh! It’s not just a platform; it’s a FREE and open source powerhouse designed to take on threat detection, prevention, and response head-on! With data aggregation from various sources, Wazuh safeguards workloads across diverse environments.
Notably, Wazuh goes above and beyond with its unified Extended Detection and Response (XDR) system and Security Information and Event Management (SIEM) system, delivering protection for your workloads.
Specifically, here’s where it gets even more incredible! The Wazuh team took OSSEC (Open Source Security) to a whole new level by forking it and unleashing a suite of mind-blowing features:
🚀 Log-based Intrusion Detection: Say goodbye to threats before they even have a chance!
🚀 Rootkit Detection: Those sneaky intruders don’t stand a chance against Wazuh’s watchful eyes!
🚀 Malware Detection: Wazuh spots malicious code from miles away and neutralizes it like a pro!
🚀 Active Response: No time to waste – Wazuh takes action to stop threats dead in their tracks!
🚀 Compliance Auditing: Leave compliance worries behind with Wazuh’s meticulous audits!
🚀 File Integrity Monitoring: Keep your files pristine and safe with Wazuh’s vigilant monitoring!
🚀 System Inventory: Wazuh knows every nook and cranny of your system for total control!
🚀 And that’s not all! There’s MORE – a whole universe of possibilities with Wazuh!
But Wait… There’s More!
But that’s not the end of it! Brace yourselves for the ultimate security experience because the Wazuh team didn’t stop there. Oh no! They built a cutting-edge API around this extraordinary functionality, ensuring seamless communication with TLS/SSL certificate technology. The result? A secure dashboard, offering unparalleled visibility into the system.
So there you have it – Wazuh is an unstoppable force of security prowess, and it’s ready to take on any challenge, leaving no room for compromise! 🔥💪🏾

A quick word on host machines
Let’s dive into the world of host machines – think of them as AirBnBs that accommodate guests. Imagine spending the night at a friend’s place, where your friend hosts you. Similarly, in the realm of computers, the computer serves as the host machine, generously sheltering various apps as guests. Now, let’s keep this excitement going!
Wazuh expressly offers an abundance of great documentation, tailor-made for developers and security engineers, all geared up to dive into action. With numerous installation options available, it is adaptable to a wide range of environments.
How to install Wazuh
To kick-start this thrilling journey, I sought out the perfect host machine for Wazuh. I choose Debian, the perfect foundation for my project (and let’s not forget, Ubuntu derives from Debian!). Provided that my Debian host up and running on Linode, I wasted no time and got straight to work. Connecting via SSH to my Linode instance, I installed Docker and Docker Compose. Once these tools were in place, I swiftly installed Wazuh-Docker, eager to unleash its potential.
With this intention, I promptly logged into the dashboard and installed the Wazuh agents. The installation process was a breeze, and soon enough, they were up and running, ready to defend my applications from any lurking threats.
With this in mind, now, let’s turn our attention to each application’s host machine. With passion and dedication, I connected to each one individually or SSH’d into them, preparing the ground for the Wazuh agents’ arrival. To emphasize, one by one, I installed these guardian applications, ensuring a formidable defense across my entire network. And there you have it! Behold the magnificent Wazuh architecture, ready to safeguard my digital realm and empower me to conquer any security challenge that comes my way. This adventure has only just begun! 🌟💻
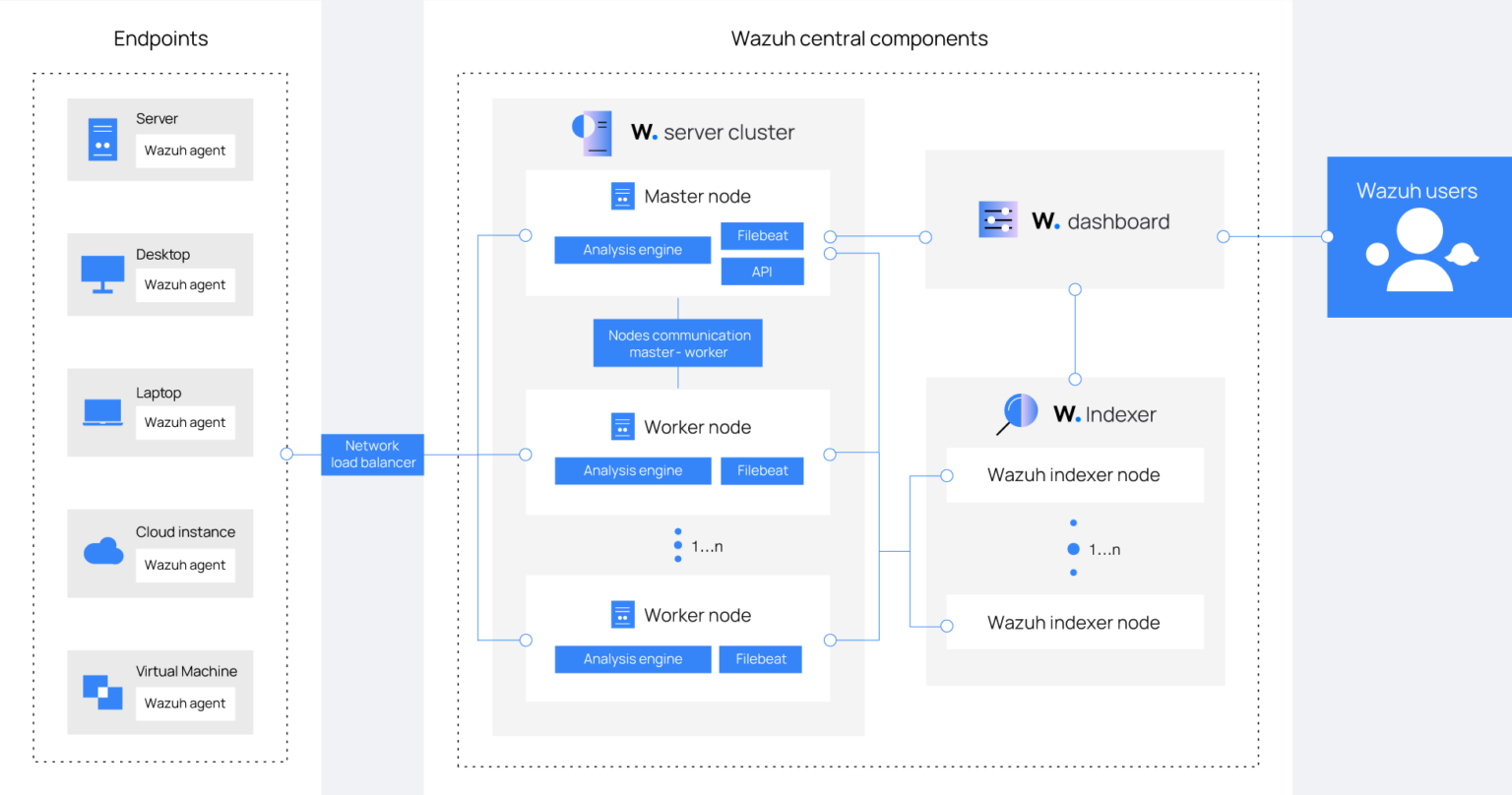
How does Wazuh work?
Taking action based on the architecture, I proactively set up the server cluster on my Debian server running flawlessly in Linode’s cloud. Thus, this powerhouse cluster, consisting of the manager, indexer, and dashboard, brought immense potential to the table.
Henceforth, I deployed agents as endpoints on my host machines. As a result, seamlessly integrating them with my other applications on Azure, Google Cloud, and Linode. Surprisingly, the synergy was undeniable! To emphasize, true to Wazuh’s reputation, the manager sprang into action immediately, receiving a barrage of alerts from the vigilant agents. These bad actors and relentless bots attempting to brute force their way into my applications were met with a formidable defense. However, I soon realized I hadn’t fortified my system with firewall rules yet, as noted by Wazuh.
Altogether, with an unwavering spirit, I captured these eye-opening alerts in a glorious screenshot, showcasing the power of Wazuh to all of you! Together, we’re unstoppable in the pursuit of security and protection! 🚀💪🏾
How to use Wazuh
To unlock the full potential of Wazuh and gain unparalleled visibility into your servers and applications, I took charge and expertly configured Wazuh. Setting up the server cluster was just the beginning; I seamlessly connected it to the agents. Following Wazuh’s top-notch documentation, I effortlessly completed this crucial step.
Opting for the Docker Single-Node installation, I swiftly executed the corresponding instructions, tailoring my Wazuh deployment to perfection. With everything up and running smoothly, I accessed the admin dashboard and was astonished to witness the relentless brute force attacks on my servers. But fear not! Wazuh not only alerted me to these attacks but also provided effective suggestions for mitigating them. To sum up, I took immediate action and safeguarded my system like a true proactive blue teamer! 💙
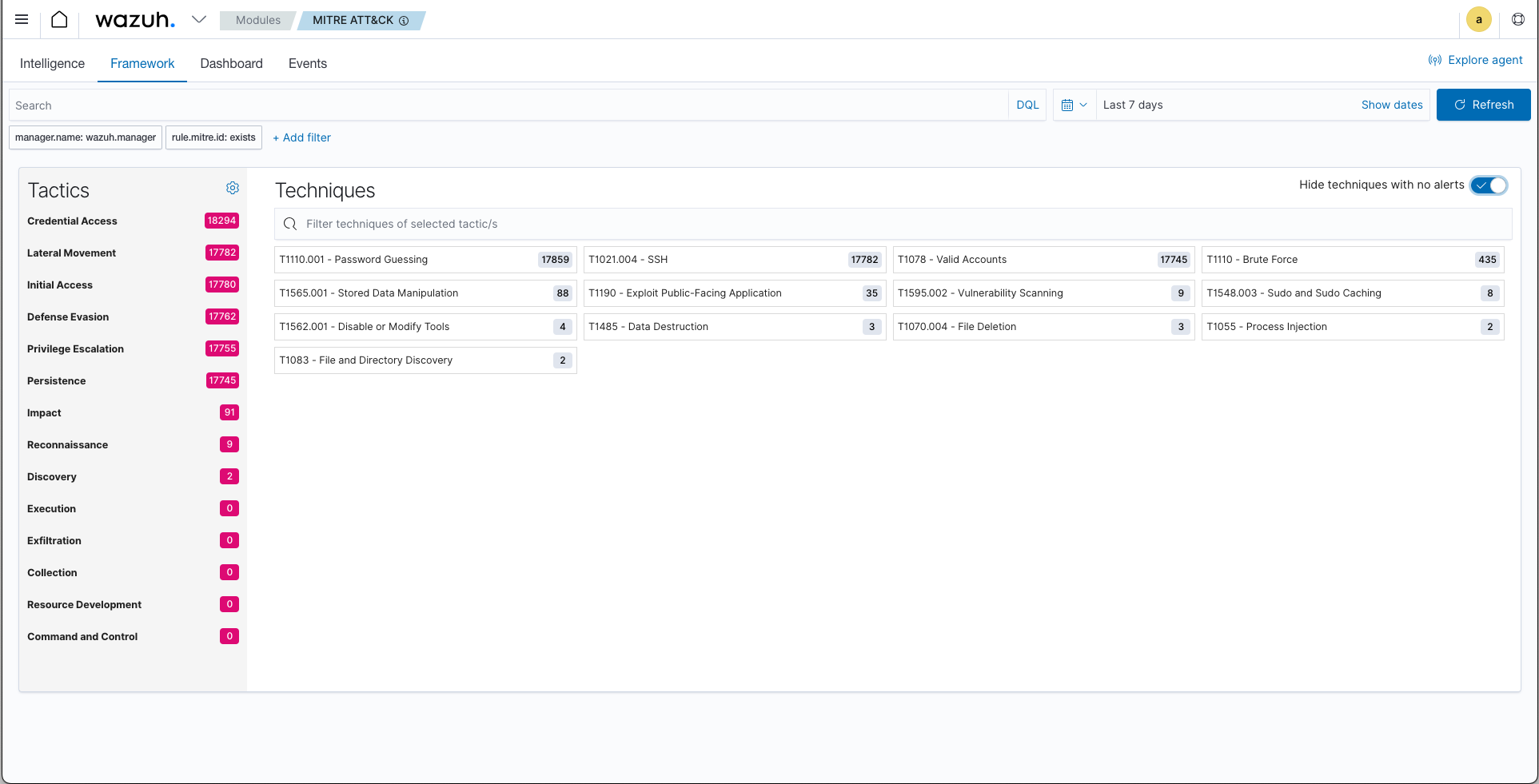
What does Wazuh do?
Wazuh provides unparalleled visibility and insights into your server(s) for Cloud Security and monitoring purposes – and the best part is, it’s completely FREE! No need to shell out extra 💰 to your cloud provider for this essential information, on top of what you’re already paying for their service(s). Stop the bleeding 🩸 🩹 now!
The filtering feature is expertly categorized based on the MITRE ATT&CK framework.
Wazuh actively manages REAL TIME File Integrity Monitoring (FIM), Vulnerability Detection, Policy Monitoring, System Auditing, Automated Log Data Analysis, and Regulatory Compliance implementation supporting PCI-DSS, NIST 800-53, TSC, GDPR and, HIPAA compliance standards.
But that’s not all. It goes beyond the basics, it provides Security Configuration Assessments (SCA) based on the Center for Information Security’s (CIS) Benchmarks hardening guides. Its Malware Detection is top-notch, capable of revealing Rootkits in your system and triggering custom Active Responses when threats are detected. For instance, you can configure it to block a known malicious IP address – an effective custom Active Response.
Wazuh… That’s What’s Up!
To the Wazuh marketing team, you can have that one. 😎 I just want the credit, for my culture. 🗽 But let’s save that discussion for another blog post on another day. Well that’s it for now. I think I’ve shared a lot here. If you’re like me, you’ll spend a lot of time in their documentation exploring the amazing features! There’s a bunch of goodies in the Proof Of Concept (PoC) Guide.
All things considered
Thank you if you’ve made it this far! Stay tuned as I will be making updates to this post and the series. I can’t leave you without my signature… If you’ve made it this far then you’re the real MVP! 🏆